Microsoft Radius Mac Authentication
- Windows Radius Mac Authentication
- Windows Server 2016 Radius Mac Authentication
- Nps Server For Radius Authentication
- Radius Mac Authentication Windows
Microsoft onenote keeps crashing mac os. Note
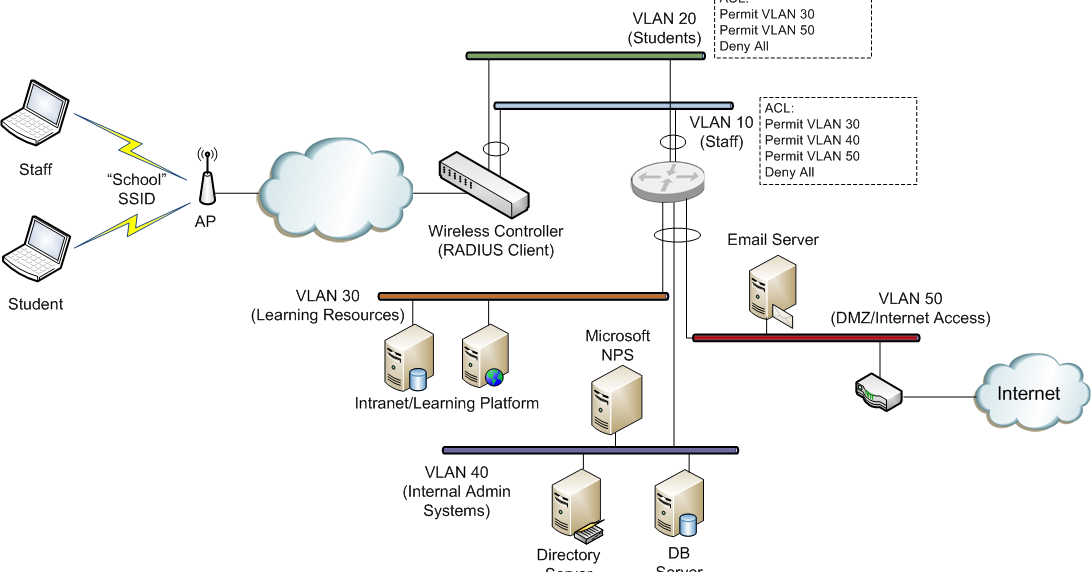
Internet Authentication Service (IAS) was renamed Network Policy Server (NPS) starting with Windows Server 2008. The content of this topic applies to both IAS and NPS. Throughout the text, NPS is used to refer to all versions of the service, including the versions originally referred to as IAS.
NPS fully supports the Remote Authentication Dial-In User Service (RADIUS) protocol. The RADIUS protocol is the de facto standard for remote user authentication and it is documented in RFC 2865 and RFC 2866.
What is Radius: Remote Authentication Dial-In User Service (RADIUS) is a client/server protocol and software that provides remote access servers to communicate with a central server to authenticate dial-in users and authorize their access to the requested system or service. Oct 06, 2017 One of the best approaches to securing cloud resources is by managing access to the network itself with the Remote Authentication Dial-In User Service (RADIUS). RADIUS allows organizations to require unique login credentials for each user on the.
RADIUS Authentication and Authorization
The following diagram shows an authenticating client ('User') connecting to a Network Access Server (NAS) over a dial-up connection, using the Point-to-Point Protocol (PPP). In order to authenticate the User, the NAS contacts a remote server running NPS. The NAS and the NPS server communicate using the RADIUS protocol.
A NAS operates as a client of a server or servers that support the RADIUS protocol. Servers that support the RADIUS protocol are generally referred to as the RADIUS servers. The RADIUS client, that is, the NAS, passes information about the User to designated RADIUS servers, and then acts on the response that the servers return. The request sent by the NAS to the RADIUS server in order to authenticate the User is generally called an 'authentication request.'
If a RADIUS server authenticates the User successfully, the RADIUS server returns configuration information to the NAS so that it can provide network service to the user. This configuration information is composed of 'authorizations' and contains, among others, the type of service NAS may provide to the User (for example, PPP, or telnet).
Windows Radius Mac Authentication
While the RADIUS server is processing the authentication request, it can perform authorization functions such as verifying the user's telephone number and checking whether the user already has a session in progress. The RADIUS server can determine whether the user already has a session in progress by contacting a state server.
For more information on RADIUS authentication and authorization, see RFC 2865.
RADIUS Accounting
The RADIUS server also collects a variety of information sent by the NAS that can be used for accounting and for reporting on network activity. The RADIUS client sends information to designated RADIUS servers when the User logs on and logs off. The RADIUS client may send additional usage information on a periodic basis while the session is in progress. The requests sent by the client to the server to record logon/logoff and usage information are generally called 'accounting requests.'
For more information on RADIUS accounting, see RFC 2866.
RADIUS Proxy
A RADIUS server can act as a proxy client to other RADIUS servers. In these cases, the RADIUS server contacted by the NAS passes the authentication or accounting request to another RADIUS server that actually performs the authentication or the accounting task.
Related topics
-->This article shows you how to create a VNet with a Point-to-Site connection that uses RADIUS authentication. This configuration is only available for the Resource Manager deployment model.
A Point-to-Site (P2S) VPN gateway lets you create a secure connection to your virtual network from an individual client computer. Point-to-Site VPN connections are useful when you want to connect to your VNet from a remote location, such as when you are telecommuting from home or a conference. A P2S VPN is also a useful solution to use instead of a Site-to-Site VPN when you have only a few clients that need to connect to a VNet.
A P2S VPN connection is started from Windows and Mac devices. Connecting clients can use the following authentication methods:
- RADIUS server
- VPN Gateway native certificate authentication
This article helps you configure a P2S configuration with authentication using RADIUS server. If you want to authenticate using generated certificates and VPN gateway native certificate authentication instead, see Configure a Point-to-Site connection to a VNet using VPN gateway native certificate authentication.
Point-to-Site connections do not require a VPN device or a public-facing IP address. P2S creates the VPN connection over either SSTP (Secure Socket Tunneling Protocol), OpenVPN or IKEv2.
SSTP is a TLS-based VPN tunnel that is supported only on Windows client platforms. It can penetrate firewalls, which makes it an ideal option to connect to Azure from anywhere. On the server side, we support SSTP versions 1.0, 1.1, and 1.2. The client decides which version to use. For Windows 8.1 and above, SSTP uses 1.2 by default.
OpenVPN® Protocol, an SSL/TLS based VPN protocol. A TLS VPN solution can penetrate firewalls, since most firewalls open TCP port 443 outbound, which TLS uses. OpenVPN can be used to connect from Android, iOS (versions 11.0 and above), Windows, Linux and Mac devices (OSX versions 10.13 and above).
IKEv2 VPN, a standards-based IPsec VPN solution. IKEv2 VPN can be used to connect from Mac devices (OSX versions 10.11 and above).
P2S connections require the following:
- A RouteBased VPN gateway.
- A RADIUS server to handle user authentication. The RADIUS server can be deployed on-premises, or in the Azure VNet.
- A VPN client configuration package for the Windows devices that will connect to the VNet. A VPN client configuration package provides the settings required for a VPN client to connect over P2S.
About Active Directory (AD) Domain Authentication for P2S VPNs
AD Domain authentication allows users to sign in to Azure using their organization domain credentials. It requires a RADIUS server that integrates with the AD server. Organizations can also leverage their existing RADIUS deployment.
The RADIUS server can reside on-premises, or in your Azure VNet. During authentication, the VPN gateway acts as a pass-through and forwards authentication messages back and forth between the RADIUS server and the connecting device. It's important for the VPN gateway to be able to reach the RADIUS server. If the RADIUS server is located on-premises, then a VPN Site-to-Site connection from Azure to the on-premises site is required.
Apart from Active Directory, a RADIUS server can also integrate with other external identity systems. This opens up plenty of authentication options for Point-to-Site VPNs, including MFA options. Check your RADIUS server vendor documentation to get the list of identity systems it integrates with.
Important
Only a VPN Site-to-Site connection can be used for connecting to a RADIUS server on-premises. An ExpressRoute connection cannot be used.
Before beginning
Verify that you have an Azure subscription. If you don't already have an Azure subscription, you can activate your MSDN subscriber benefits or sign up for a free account.
Working with Azure PowerShell
This article uses PowerShell cmdlets. To run the cmdlets, you can use Azure Cloud Shell. The Azure Cloud Shell is a free interactive shell that you can use to run the steps in this article. It has common Azure tools preinstalled and configured to use with your account.
To open the Cloud Shell, just select Try it from the upper right corner of a code block. You can also launch Cloud Shell in a separate browser tab by going to https://shell.azure.com/powershell. Select Copy to copy the blocks of code, paste it into the Cloud Shell, and press enter to run it.
You can also install and run the Azure PowerShell cmdlets locally on your computer. PowerShell cmdlets are updated frequently. If you have not installed the latest version, the values specified in the instructions may fail. To find the versions of Azure PowerShell installed on your computer, use the Get-Module -ListAvailable Az cmdlet. To install or update, see Install the Azure PowerShell module.
Example values
You can use the example values to create a test environment, or refer to these values to better understand the examples in this article. You can either use the steps as a walk-through and use the values without changing them, or change them to reflect your environment.
- Name: VNet1
- Address space: 192.168.0.0/16 and 10.254.0.0/16
For this example, we use more than one address space to illustrate that this configuration works with multiple address spaces. However, multiple address spaces are not required for this configuration. - Subnet name: FrontEnd
- Subnet address range: 192.168.1.0/24
- Subnet name: BackEnd
- Subnet address range: 10.254.1.0/24
- Subnet name: GatewaySubnet
The Subnet name GatewaySubnet is mandatory for the VPN gateway to work.- GatewaySubnet address range: 192.168.200.0/24
- VPN client address pool: 172.16.201.0/24
VPN clients that connect to the VNet using this Point-to-Site connection receive an IP address from the VPN client address pool. - Subscription: If you have more than one subscription, verify that you are using the correct one.
- Resource Group: TestRG
- Location: East US
- DNS Server: IP address of the DNS server that you want to use for name resolution for your VNet. (optional)
- GW Name: Vnet1GW
- Public IP name: VNet1GWPIP
- VpnType: RouteBased
1. Set the variables
Declare the variables that you want to use. Use the following sample, substituting the values for your own when necessary. If you close your PowerShell/Cloud Shell session at any point during the exercise, just copy and paste the values again to re-declare the variables.
2. Create the resource group, VNet, and Public IP address
The following steps create a resource group and a virtual network in the resource group with three subnets. When substituting values, it's important that you always name your gateway subnet specifically 'GatewaySubnet'. If you name it something else, your gateway creation fails;
Create a resource group.
Create the subnet configurations for the virtual network, naming them FrontEnd, BackEnd, and GatewaySubnet. These prefixes must be part of the VNet address space that you declared.
Create the virtual network.
In this example, the -DnsServer server parameter is optional. Specifying a value does not create a new DNS server. The DNS server IP address that you specify should be a DNS server that can resolve the names for the resources you are connecting to from your VNet. For this example, we used a private IP address, but it is likely that this is not the IP address of your DNS server. Be sure to use your own values. The value you specify is used by the resources that you deploy to the VNet, not by the P2S connection.
A VPN gateway must have a Public IP address. You first request the IP address resource, and then refer to it when creating your virtual network gateway. The IP address is dynamically assigned to the resource when the VPN gateway is created. VPN Gateway currently only supports Dynamic Public IP address allocation. You cannot request a Static Public IP address assignment. However, this does not mean that the IP address changes after it has been assigned to your VPN gateway. The only time the Public IP address changes is when the gateway is deleted and re-created. It doesn't change across resizing, resetting, or other internal maintenance/upgrades of your VPN gateway.
Specify the variables to request a dynamically assigned Public IP address.
3. Set up your RADIUS server
Before creating and configuring the virtual network gateway, your RADIUS server should be configured correctly for authentication.
- If you don’t have a RADIUS server deployed, deploy one. For deployment steps, refer to the setup guide provided by your RADIUS vendor.
- Configure the VPN gateway as a RADIUS client on the RADIUS. When adding this RADIUS client, specify the virtual network GatewaySubnet that you created.
- Once the RADIUS server is set up, get the RADIUS server's IP address and the shared secret that RADIUS clients should use to talk to the RADIUS server. If the RADIUS server is in the Azure VNet, use the CA IP of the RADIUS server VM.
The Network Policy Server (NPS) article provides guidance about configuring a Windows RADIUS server (NPS) for AD domain authentication.
4. Create the VPN gateway
Configure and create the VPN gateway for your VNet.
- The -GatewayType must be 'Vpn' and the -VpnType must be 'RouteBased'.
- A VPN gateway can take up to 45 minutes to complete, depending on the gateway SKU you select.
5. Add the RADIUS server and client address pool
- The -RadiusServer can be specified by name or by IP address. If you specify the name and the server resides on-premises, then the VPN gateway may not be able to resolve the name. If that’s the case, then it's better to specify the IP address of the server.
- The -RadiusSecret should match what is configured on your RADIUS server.
- The -VpnClientAddressPool is the range from which the connecting VPN clients receive an IP address. Use a private IP address range that does not overlap with the on-premises location that you will connect from, or with the VNet that you want to connect to. Ensure that you have a large enough address pool configured.
Create a secure string for the RADIUS secret.
You are prompted to enter the RADIUS secret. The characters that you enter will not be displayed and instead will be replaced by the '*' character.
Add the VPN client address pool and the RADIUS server information.
For SSTP configurations:
For OpenVPN® configurations:
For IKEv2 configurations:
For SSTP + IKEv2
6. Download the VPN client configuration package and set up the VPN client
The VPN client configuration lets devices connect to a VNet over a P2S connection. To generate a VPN client configuration package and set up the VPN client, see Create a VPN Client Configuration for RADIUS authentication.
Windows Server 2016 Radius Mac Authentication
7. Connect to Azure
To connect from a Windows VPN client
To connect to your VNet, on the client computer, navigate to VPN connections and locate the VPN connection that you created. It is named the same name as your virtual network. Enter your domain credentials and click 'Connect'. A pop-up message requesting elevated rights appears. Accept it and enter the credentials.
Your connection is established.
Connect from a Mac VPN client
From the Network dialog box, locate the client profile that you want to use, then click Connect.
To verify your connection
To verify that your VPN connection is active, open an elevated command prompt, and run ipconfig/all.
View the results. Notice that the IP address you received is one of the addresses within the Point-to-Site VPN Client Address Pool that you specified in your configuration. The results are similar to this example:
To troubleshoot a P2S connection, see Troubleshooting Azure point-to-site connections.
To connect to a virtual machine
You can connect to a VM that is deployed to your VNet by creating a Remote Desktop Connection to your VM. The best way to initially verify that you can connect to your VM is to connect by using its private IP address, rather than computer name. That way, you are testing to see if you can connect, not whether name resolution is configured properly.
Locate the private IP address. You can find the private IP address of a VM by either looking at the properties for the VM in the Azure portal, or by using PowerShell.
Azure portal - Locate your virtual machine in the Azure portal. View the properties for the VM. The private IP address is listed.
PowerShell - Use the example to view a list of VMs and private IP addresses from your resource groups. You don't need to modify this example before using it.
Verify that you are connected to your VNet using the Point-to-Site VPN connection.
Open Remote Desktop Connection by typing 'RDP' or 'Remote Desktop Connection' in the search box on the taskbar, then select Remote Desktop Connection. You can also open Remote Desktop Connection using the 'mstsc' command in PowerShell.
In Remote Desktop Connection, enter the private IP address of the VM. You can click 'Show Options' to adjust additional settings, then connect.
To troubleshoot an RDP connection to a VM
If you are having trouble connecting to a virtual machine over your VPN connection, check the following:
- Verify that your VPN connection is successful.
- Verify that you are connecting to the private IP address for the VM.
- Use 'ipconfig' to check the IPv4 address assigned to the Ethernet adapter on the computer from which you are connecting. If the IP address is within the address range of the VNet that you are connecting to, or within the address range of your VPNClientAddressPool, this is referred to as an overlapping address space. When your address space overlaps in this way, the network traffic doesn't reach Azure, it stays on the local network.
- If you can connect to the VM using the private IP address, but not the computer name, verify that you have configured DNS properly. For more information about how name resolution works for VMs, see Name Resolution for VMs.
- Verify that the VPN client configuration package was generated after the DNS server IP addresses were specified for the VNet. If you updated the DNS server IP addresses, generate and install a new VPN client configuration package.
- For more information about RDP connections, see Troubleshoot Remote Desktop connections to a VM.
FAQ
This FAQ applies to P2S using RADIUS authentication
How many VPN client endpoints can I have in my Point-to-Site configuration?
It depends on the gateway SKU. For more information on the number of connections supported, see Gateway SKUs.
What client operating systems can I use with Point-to-Site?
The following client operating systems are supported:
- Windows 7 (32-bit and 64-bit)
- Windows Server 2008 R2 (64-bit only)
- Windows 8.1 (32-bit and 64-bit)
- Windows Server 2012 (64-bit only)
- Windows Server 2012 R2 (64-bit only)
- Windows Server 2016 (64-bit only)
- Windows 10
- Mac OS X version 10.11 or above
- Linux (StrongSwan)
- iOS
Note
Starting July 1, 2018, support is being removed for TLS 1.0 and 1.1 from Azure VPN Gateway. VPNGateway will support only TLS 1.2. To maintain support, see the updates to enable support for TLS1.2.
Additionally, the following legacy algorithms will also be deprecated for TLS on July 1, 2018:
- RC4 (Rivest Cipher 4)
- DES (Data Encryption Algorithm)
- 3DES (Triple Data Encryption Algorithm)
- MD5 (Message Digest 5)
How do I enable support for TLS 1.2 in Windows 7 and Windows 8.1?
Open a command prompt with elevated privileges by right-clicking on Command Prompt and selecting Run as administrator.
Run the following commands in the command prompt:
Install the following updates:
Reboot the computer.
Connect to the VPN.
Note
You will have to set the above registry key if you are running an older version of Windows 10 (10240).
Can I traverse proxies and firewalls using Point-to-Site capability?
Azure supports three types of Point-to-site VPN options:
Secure Socket Tunneling Protocol (SSTP). SSTP is a Microsoft proprietary SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses.
OpenVPN. OpenVPN is a SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses.
IKEv2 VPN. IKEv2 VPN is a standards-based IPsec VPN solution that uses outbound UDP ports 500 and 4500 and IP protocol no. 50. Firewalls do not always open these ports, so there is a possibility of IKEv2 VPN not being able to traverse proxies and firewalls.
If I restart a client computer configured for Point-to-Site, will the VPN automatically reconnect?
By default, the client computer will not reestablish the VPN connection automatically.
Does Point-to-Site support auto-reconnect and DDNS on the VPN clients?
Auto-reconnect and DDNS are currently not supported in Point-to-Site VPNs.
Can I have Site-to-Site and Point-to-Site configurations coexist for the same virtual network?
Yes. For the Resource Manager deployment model, you must have a RouteBased VPN type for your gateway. For the classic deployment model, you need a dynamic gateway. We do not support Point-to-Site for static routing VPN gateways or PolicyBased VPN gateways.
Can I configure a Point-to-Site client to connect to multiple virtual network gateways at the same time?
Depending on the VPN Client software used, you may be able to connect to multiple Virtual Network Gateways provided the virtual networks being connected to do not have conflicting address spaces between them or the network from with the client is connecting from. While the Azure VPN Client supports many VPN connections, only one connection can be Connected at any given time.
Can I configure a Point-to-Site client to connect to multiple virtual networks at the same time?
Yes, Point-to-Site connections to a Virtual Network Gateway deployed in a VNet that is peered with other VNets may have access to other peered VNets. Provided the peered VNets are using the UseRemoteGateway / AllowGatewayTransit features, the Point-to-Site client will be able to connect to those peered VNets. For more information please reference this article.
How much throughput can I expect through Site-to-Site or Point-to-Site connections?
It's difficult to maintain the exact throughput of the VPN tunnels. IPsec and SSTP are crypto-heavy VPN protocols. Throughput is also limited by the latency and bandwidth between your premises and the Internet. For a VPN Gateway with only IKEv2 Point-to-Site VPN connections, the total throughput that you can expect depends on the Gateway SKU. For more information on throughput, see Gateway SKUs.
Can I use any software VPN client for Point-to-Site that supports SSTP and/or IKEv2?
No. You can only use the native VPN client on Windows for SSTP, and the native VPN client on Mac for IKEv2. However, you can use the OpenVPN client on all platforms to connect over OpenVPN protocol. Refer to the list of supported client operating systems.
Does Azure support IKEv2 VPN with Windows?
IKEv2 is supported on Windows 10 and Server 2016. However, in order to use IKEv2, you must install updates and set a registry key value locally. OS versions prior to Windows 10 are not supported and can only use SSTP or OpenVPN® Protocol.
To prepare Windows 10 or Server 2016 for IKEv2:
Install the update.
OS version Date Number/Link Windows Server 2016
Windows 10 Version 1607January 17, 2018 KB4057142 Windows 10 Version 1703 January 17, 2018 KB4057144 Windows 10 Version 1709 March 22, 2018 KB4089848 Set the registry key value. Create or set “HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesRasMan IKEv2DisableCertReqPayload” REG_DWORD key in the registry to 1.
What happens when I configure both SSTP and IKEv2 for P2S VPN connections?
When you configure both SSTP and IKEv2 in a mixed environment (consisting of Windows and Mac devices), the Windows VPN client will always try IKEv2 tunnel first, but will fall back to SSTP if the IKEv2 connection is not successful. MacOSX will only connect via IKEv2.
Other than Windows and Mac, which other platforms does Azure support for P2S VPN?
Azure supports Windows, Mac and Linux for P2S VPN.
I already have an Azure VPN Gateway deployed. Can I enable RADIUS and/or IKEv2 VPN on it?
Yes, you can enable these new features on already deployed gateways using Powershell or the Azure portal, provided that the gateway SKU that you are using supports RADIUS and/or IKEv2. For example, the VPN gateway Basic SKU does not support RADIUS or IKEv2.
How do I remove the configuration of a P2S connection?
A P2S configuration can be removed using Azure CLI and PowerShell using the following commands:
Azure PowerShell
Azure CLI
Is RADIUS authentication supported on all Azure VPN Gateway SKUs?
RADIUS authentication is supported for VpnGw1, VpnGw2, and VpnGw3 SKUs. If you are using legacy SKUs, RADIUS authentication is supported on Standard and High Performance SKUs. It is not supported on the Basic Gateway SKU.
Is RADIUS authentication supported for the classic deployment model?
No. RADIUS authentication is not supported for the classic deployment model.
Are 3rd-party RADIUS servers supported?
Yes, 3rd-party RADIUS servers are supported.
What are the connectivity requirements to ensure that the Azure gateway is able to reach an on-premises RADIUS server?
A VPN Site-to-Site connection to the on-premises site, with the proper routes configured, is required.
Can traffic to an on-premises RADIUS server (from the Azure VPN gateway) be routed over an ExpressRoute connection?
No. It can only be routed over a Site-to-Site connection.
Is there a change in the number of SSTP connections supported with RADIUS authentication? What is the maximum number of SSTP and IKEv2 connections supported?
There is no change in the maximum number of SSTP connections supported on a gateway with RADIUS authentication. It remains 128 for SSTP, but depends on the gateway SKU for IKEv2. For more information on the number of connections supported, see Gateway SKUs.
What is the difference between doing certificate authentication using a RADIUS server vs. using Azure native certificate authentication (by uploading a trusted certificate to Azure).
In RADIUS certificate authentication, the authentication request is forwarded to a RADIUS server that handles the actual certificate validation. This option is useful if you want to integrate with a certificate authentication infrastructure that you already have through RADIUS.
When using Azure for certificate authentication, the Azure VPN gateway performs the validation of the certificate. You need to upload your certificate public key to the gateway. You can also specify list of revoked certificates that shouldn’t be allowed to connect.
Does RADIUS authentication work with both IKEv2, and SSTP VPN?
Nps Server For Radius Authentication
Yes, RADIUS authentication is supported for both IKEv2, and SSTP VPN.
Radius Mac Authentication Windows
Does RADIUS authentication work with the OpenVPN client?
RADIUS authentication is supported for the OpenVPN protocol only through PowerShell.
Next steps
Once your connection is complete, you can add virtual machines to your virtual networks. For more information, see Virtual Machines. To understand more about networking and virtual machines, see Azure and Linux VM network overview.